Cleaning up stupid Mac malware: “ProjectX”

"Becoming is certainly not imitating, or identifying with something; neither is it regressing-progressing; neither is it corresponding, establishing corresponding relations; neither is it producing, producing a filiation or producing through filiation. Becoming is a verb with a consistency all its own; it does not reduce to, or lead back to, appearing,"
– Gilles Deluze and Félix Guattari, A Thousand Plateaus
I thought it would be useful to describe the research and removal process of a recent support case involving a faculty member who had inadvertently gotten some malware. What I didn’t realize was the strange story of becoming and identity hidden in this seemingly simple procedure. I didn’t expect to be thrown into confusion at the mysterious person, identified in many ways throughout the course of my investigation, but most interestingly so, as simply “V”.
All of our laptop users, both faculty and student, have administrative rights on their laptops. This is an important decision to us, and we feel strongly about continuing to grant those privileges. However, sometimes users can get into trouble, particularly when it comes to misleading software offering to be “helpful”, as we will see. It is this administrative privilege which can lead to serious issues. Fortunately, the malware involved in this particular instance is pretty stupid. I know if I was a dirtbag malware author and I was granted admin privileges as part of a software installation process, I can think of a lot better things to do than to just hijack Webkit’s default search engine and home page…
When I received the laptop, it had a ton of junky popup-laden websites with audio informing me that this laptop was infected with a virus, and I should call a phone number right away. After working with the laptop a little bit, it became apparent that the symptoms were limited to Chrome and Safari, and were:
- An inability to set and retain a HomePage after browser restarts.
- Search omnibar set to Google in preferences, yet getting sent to Yahoo.
- eCommerce sites like Amazon have an obtrusive overlay of other products from an unrelated site.
- All cookies are accepted. If preference is changed, it gets reset to allow all cookies upon browser restart.
I have cleaned several of these things in the last few weeks, so clearly I can expect to see more in the future. This one in particular was masquerading as an FLV video player. I imagine the user found a video somewhere and couldn’t figure out how to play it. (I haven’t been able to figure out where or what the user searched for). “FLVPlayer1” was there to help.
The user downloaded the disk image, mounted it, and ran the “installer” app contained within. Soon after, the user found that Safari and Chrome both kept setting the home page, despite reset/quit/restart cycles, to “www.only-search.com”. Also, searches from the omnibar were redirected to “only-search”, despite the preferences clearly stating that Google was the default search engine.
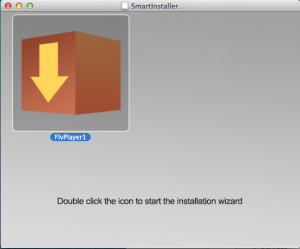
Astute users would probably notice right away that this doesn’t look like a standard installer package or drag-n-drop application wrapped in a dmg. Because it isn’t. Also, notice the strange disk image name “SmartInstaller”… The disk image file is named FlvPlayer1.dmg, but is mounted as SmartInstaller. My guess on this is that “SmartInstaller”, and probably a lot of the later code, is written by some individual who then sells his product to would-be ransomers, who can customize the product to their needs (point it to their particular ransom website, make it look like something useful in particular—in this case a video player).
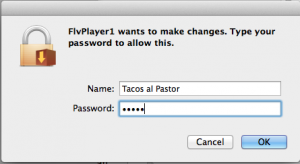
The first thing it does is ask for an admin password, which is the last thing that a legit installer does.
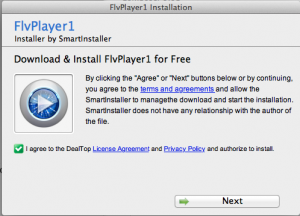
Here we can see that the installer program clearly does not look like an installer package. Why, malware author, not use the package format to make your installer look more legit? I’m not sure. I don’t see anything in the installed payload that wouldn’t work through a standard package. Again, this points to a customizable product; specifically, it’s probably set up so that someone with no knowledge of OS-specific deployment technologies can get up and running quickly. I’m sure there’s a Windows version of “SmartInstaller”/ProjectX as well.
Anyway, tellingly, the “I agree” checkbox for the “License Agreement” and “Privacy Policy” doesn’t actually allow you to deselect it. If you continue, you are agreeing. If you follow the links in the app I came across, they lead to website with an unfamilar name, “deal-top.com”. We’ve gone from FlvPlayer1 to SmartInstaller to deal-top. Here are the links: Terms of Use and Privacy Policy, which seem like pretty boilerplate legalese letting those interested enough in reading them that Deal Top can basically do anything they want.
Deal Top is described as a browser plugin that offers you alternate shopping opportunities (from a FLVPlayer?) and mentions specifically that you’re welcome to uninstall it from the Internet Explorer, Chrome, or Firefox browser (my user uses Safari…). If you browse onto the other pages on the website, it’s pretty sparse.
There’s a download link which results in a disk image named “MPlayerX.dmg”, not “FlvPlayer1.dmg”. Once mounted, they look strangely similar, although not identical: 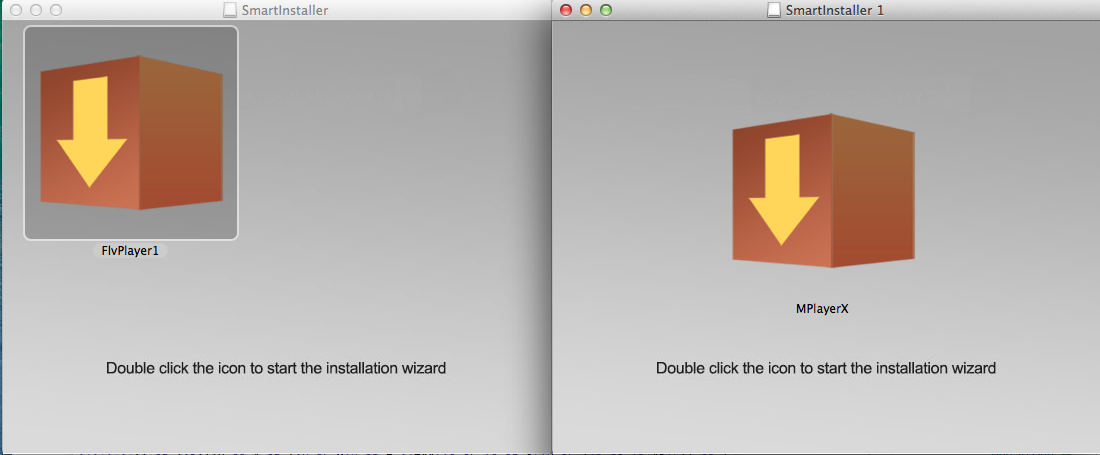
I took a look at the binary contained within, and sure enough, they’re identical. So “Deal Top”’s purported browser plugin is actually named “MPlayerX.dmg”? That sounds more like a… media player? Right? And it is identical to the “FlvPlayer1” which brought us here in the first place.
There is an amusing link at the bottom, “Uninstall”, which leads to a new site: www.smart-installer.com. The “uninstall” information is, actually, basically what I’m going to tell you to do!
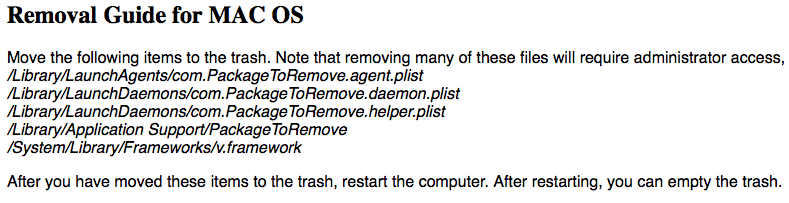
This “smart-installer.com” site must be the destination for a lot of “Uninstall” links, since you’ll notice that the identifier for the LaunchAgents and LaunchDaemons only read “PackageToRemove”… Probably because there are hundred if not thousands of “Deal Top”-like sites and installers pointing to it.
Since the Terms of Use mention Internet Explorer, I assumed that there would be a separate set of instructions for uninstalling on Windows. There aren’t. Just to be sure, I used curl to download the uninstall page with a different user agent, but got the same thing. I did see that smart-installer.com is being served by nginx, so the mysterious author must be somewhat current.
By the way, www.smart-installer.com src is just an html tag with an empty head and an empty body. Curious.
I did a whois lookup on the websites mentioned above, without much useful information. Most of them are registered by www.enom.com, which is in term registered by GoDaddy. eNom is apparently based in Kirkland, WA, and you can read about them from the Better Business Bureau here. According to their Twitter profile, they are a wholesaler of domain names. “deal-top.com” is registered by namecheap.com, and is protected by their “whoisguard” product, which makes getting any information about who actually owns these websites difficult to ascertain.
Looking at the actual compiled code for the installer, I found a certificate chain that includes this mysterious entry: 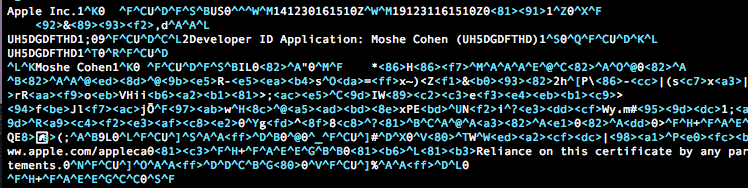
Who is this mysterious “Moshe Cohen”? Googling different things with “Moshe Cohen flv player” (should I use only-search.com to look him up?) gives a top hit of this blog post about how to use Chrome to download videos from Facebook. But the article itself is not related to Moshe, rather, this comment:
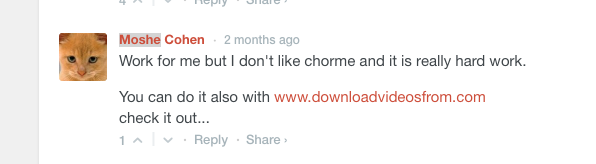
I’m not confident that it’s the same Moshe Cohen. Who knows.
Running the installer app through pkgutil’s –check-signature seems to check out: 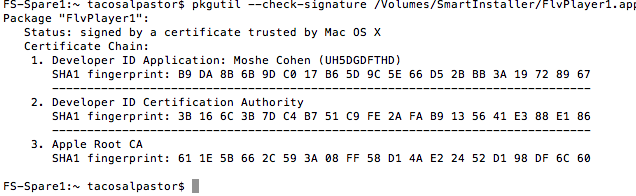
I’d be interested to see if there’s some way to see get information on a valid, registered Apple Developer.
Digging around in the installer some more, you can find this:
Specifically, references to SIMBL, which is short for “Simple Bundle Loader”. Check out the Wikipedia page. It allows you to load code into an application to manipulate it in ways that the original developer did not provide. A nice way of referring to them would be “unofficial plugins”, and a not so nice way would be “hacks”. I’m not sure that SIMBL stuff even works any more… Still, there’s a lot of references to PolarSSL, which is ominous.
Further digging, and lo! More mystery!
Buried deep in the agent, is a twisted koan of some kind: /Library/Application Support/projectX/Agent/agent.app/Contents/Resources/en.lproj/Credits.rtf reads (in its entirety):
**Engineering:** Some people **Human Interface Design:** Some other people **Testing:** Hopefully not nobody **Documentation:** Whoever **With special thanks to:** Mom
Now, this is something! It goes from sarcasm to worry to nihilism to familial gratitude in a rollercoaster haiku of a few mere lines. Somewhere out there, a deeply questioning V wants his mother to know, despite their estrangement, that he still thinks fondly of her.
Who is testing? Hopefully not nobody! Who has documented this undertaking? Whoever? Perhaps nobody. Perhaps someone. It is unimportant. Documentation is in the past, a dead thing. V is only interested in moving forward, (Engineering: some people, living, breathing, thinking beings with lives and families)
Anyway, back to the installer.
Amusingly, it gives you the sham option of a “Quick (Recommended)” install, and an “Advanced” install. (Sorry, forgot to make a screenshot).
Here are the files installed by our installer: 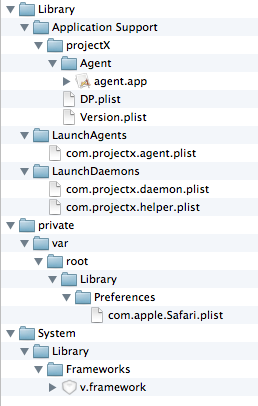
Just for down-and-dirty research, I used JAMF’s Composer to track filesystem changes and generate the list above. I’ve removed the cruft from the application saved-state caching system, etc, and just left the files installed by “Smart Installer”.
So, we’re looking at a system framework, and an executable hidden in Application Support, that is run and updated through a few LaunchAgents and LaunchDaemons.
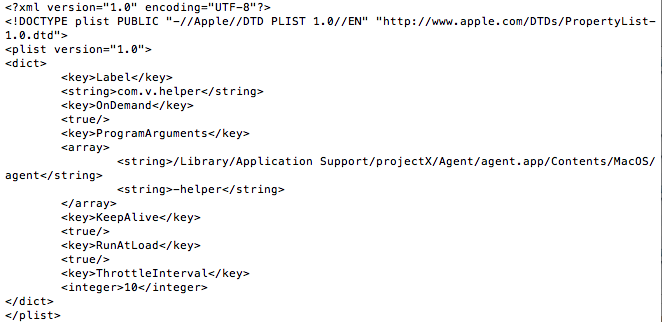
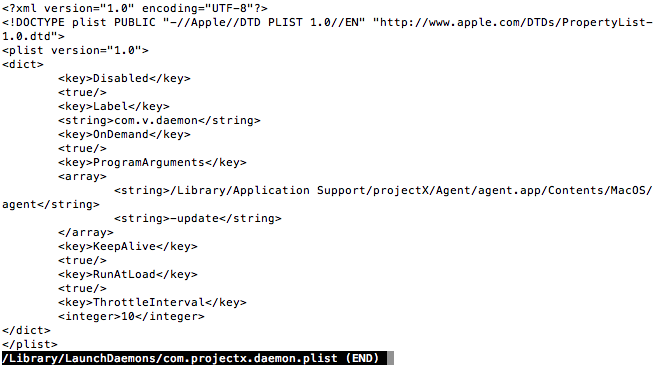
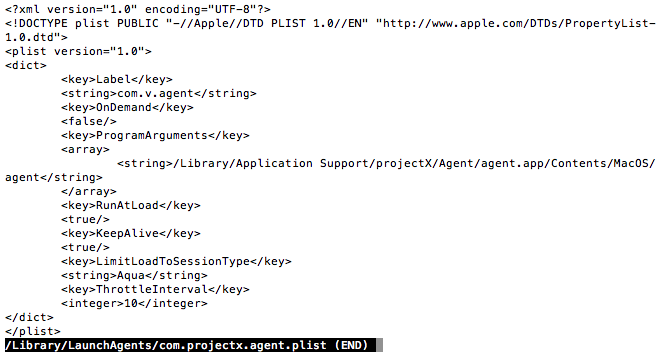
All of these LaunchD jobs load the “Agent” included in the Application Support folder, with different commandline arguments. I did some quick tcpdumps of “agent”, running with each of the commandline arguments, and didn’t find anything.
Notice, also, that the name has changed again. No longer “Smart Installer”, “FLVPlayer1”, or “Deal Top”. Now we’re looking at the sinisterly-named “projectx” (as per the reversed identifier). Perhaps as some kind of obfuscation, the identifier specified in each plist is different. For example, com.projectx.agent.plist shows up in LaunchD as “com.v.agent”. Being a fan of Pynchon, this new moniker, simply “V”, appeals to me.
The installer finishes pretty quickly, and, TADA! Nothing happens. In fact, NOTHING happens. I’m surprised that it doesn’t postinstall script start those LaunchDaemons. No, you have to reboot to get them active. Once you do, however, your home page is changed: 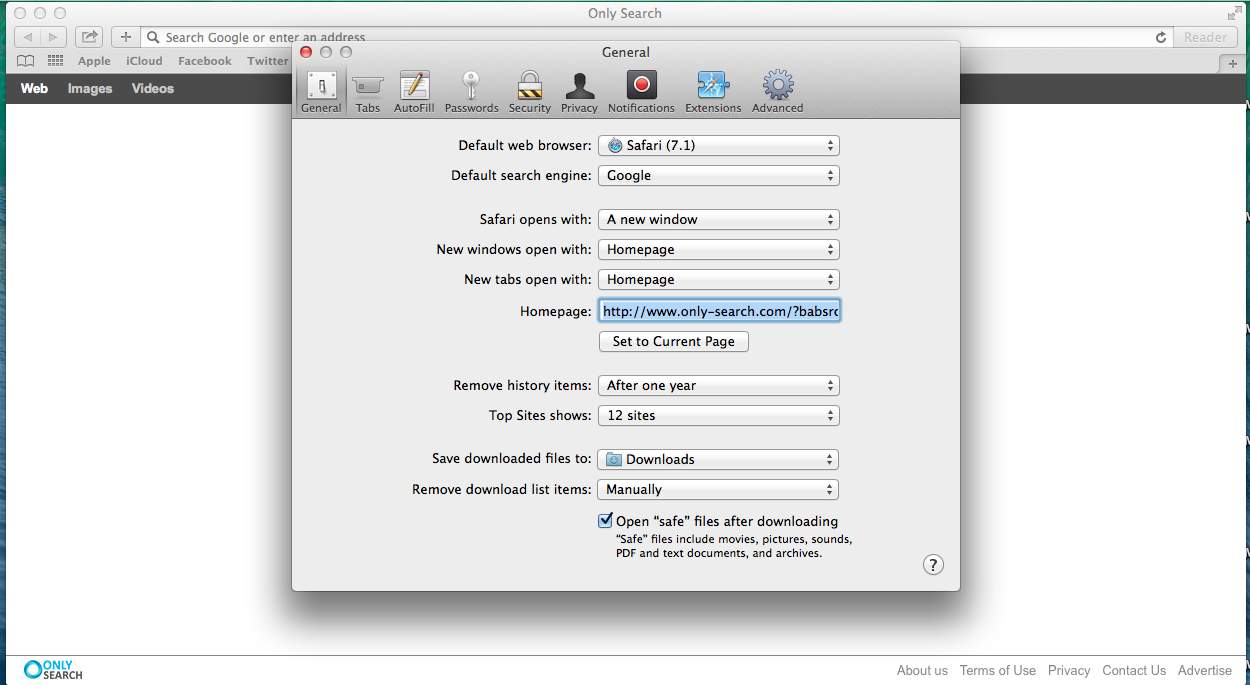
You can change it back to whatever you like, but upon restarting Safari, it is restored to “www-only-search.com”. This is what the “agent” is doing in the background-making sure that certain preferences are set how “they” (be they Moshe Cohen, Deal Top, “V”, etc) want it.
Another change is that it sets the cookie policy to allow all cookies. This is a key in com.apple.Safari.plist. The installer sets it in the root preference domain, at /var/root/Library/Preferences/com.apple.Safari.plist. The “agent” enforces the setting, however, only in the user domain.
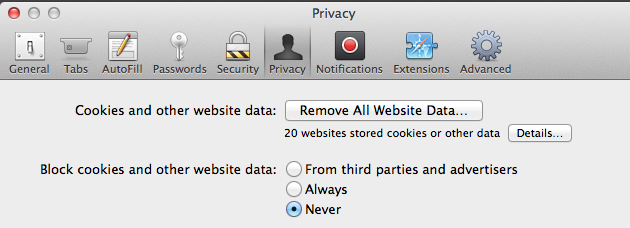
I dumped all cookies from my test machine and quit Safari, and then restarted Safari. Very quickly, I could see a bunch of cookies being added to the cookie store. There must be some traffic going on in the background. After two restarts I had 36 cookies.
If you toggle the cookie setting to block “Always”, upon the next restart, the user preference is restored to “Never”. This happens regardless of whether you change or delete the preference with defaults delete/write, or toggle it in the preferences dialog. (The keys are WebKitStorageBlockingPolicy and “com.apple.Safari.ContentPageGroupIdentifier.WebKit2StorageBlockingPolicy”. 0 is “Never”, and 2 is “Always”)
It took me a little while to figure out what else was happening. While it’s annoying to have all of your omnibar searches pumped through Yahoo, that’s not that bad. Eventually I decided to trust in the Terms of Use and try to engage in some e-commerce. Well, well!
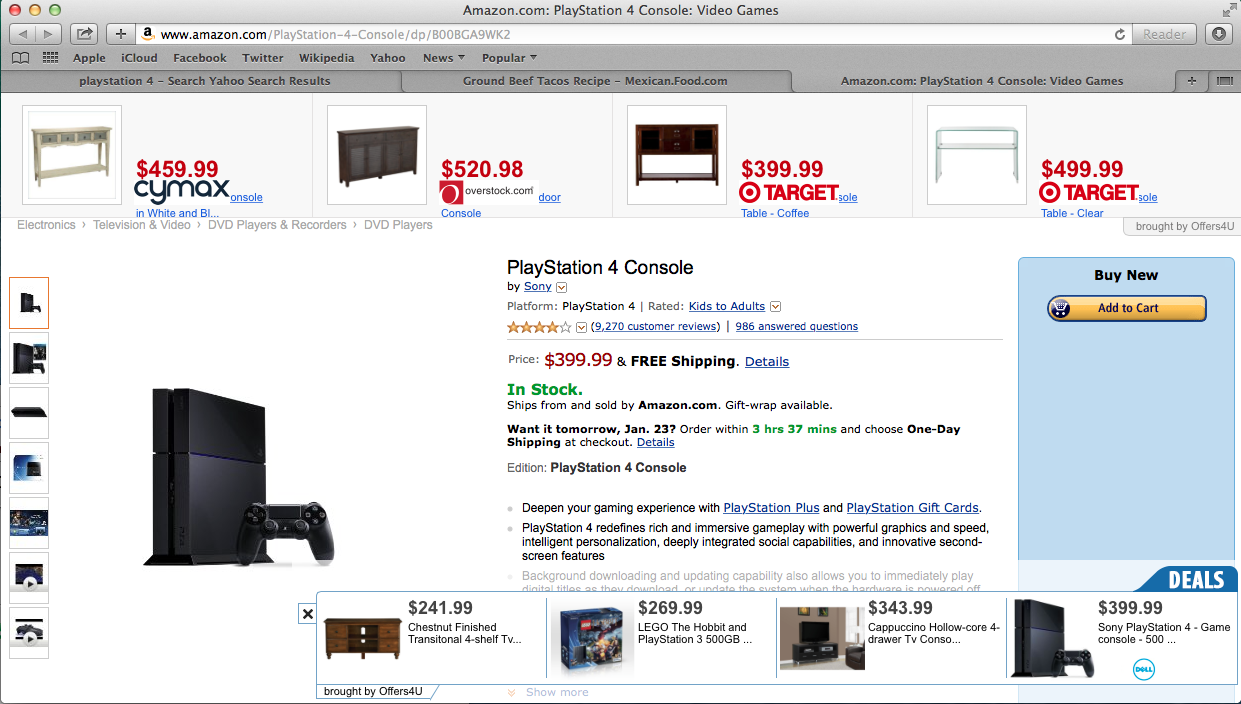
That’s not the Amazon we all know. There is actually an overlay, just like Deal Top promised. Perhaps “V” is actually an upstanding entrepreneur. I made a packet capture with tcpdump while surfing around Amazon on an infected computer and, despite my relatively weak Wireshark skills, quickly identified some interesting traffic. A lot of extra traffic was going to some IP’s which included “www.superfish.com” in their requests. Superfish seems to be a legitimate visual search product, but if you search for “superfish malware” there does indeed seem to be a shopping “virus” named superfish. I plugged the IP address into whois and interestingly enough, a new name appeared. A “Grahame Cohen” is listed for a range of several IPs. Is this a relative of Moshe’s? A brother? I think it’s just another one of V’s shifting personalities, an alter-ego amongst many.
Not to mention, there’s also a little handle on the overlays labeled “Offers4U”, just to add to the list of monikers, shell businesses, and mystery. In reality, all of this trouble seems to be an attempt to send as much web traffic through bizrate.com as possible to generate ad pay-per-click revenues. This is click fraud-check it out. It’s a huge industry. Unfortunately, I don’t know how to trace the pay-per-clicks to figure out who gets the money; who benefits from V’s deception?
After all of that, how do we clean this stuff up? It’s actually quite simple. The quick and dirty approach is to just delete the files installed and reboot. Just to be nerdy, I like to unload them first just to be safe. So here’s how it’s done.
$ #### Sudo in and unload/disable LaunchD jobs.
$ sudo su -
$ launchctl unload -w /Library/LaunchDaemons/com.projectx.*
launchctl: Error unloading: com.v.daemon
$ #### Interesting that the "daemon" wasn't actually loaded...
$ launchctl unload -w /Library/LaunchAgents/com.projectx.agent.plist
$ launchctl list | grep com\.v\..
$ ### (Nothing to report)
$ ### Remove files...
$ rm -rf /Library/Application\ Support/projectX /Library/Launch*/com.projectx.*.plist /System/Library/Frameworks/v.framework
$ ### Fix cookie preferences
$ defaults delete com.apple.Safari WebKitStorageBlockingPolicy
$ defaults delete com.apple.Safari "com.apple.Safari.ContentPageGroupIdentifier.WebKit2StorageBlockingPolicy"
$ ### (Alternately, defaults write to set them to 1 or 2)
$ exit
$ #### Back to "me".
$ defaults delete com.apple.Safari WebKitStorageBlockingPolicy
$ defaults delete com.apple.Safari "com.apple.Safari.ContentPageGroupIdentifier.WebKit2StorageBlockingPolicy"
$ defaults write com.apple.Safari HomePage "http://slashdot.org"(This is a simulated bash session. Feel free to make a script to do this, although the names will probably all be different the next time you come across it)
A reboot probably wouldn’t hurt. After all of this, things should be back to normal.
This procedure is probably pretty similar across a variety of these “products”; just look for LaunchAgents/LaunchDaemons in the system domain and see what files they reference. At some point I plan on writing a little script to automate some of the research that goes on for this so that you can quickly and easily remove these things.
I look forward to my next adware removal. I want to see if V is involved. Has he or she advanced in skill? Are there any more clues as to his mental state? How is his mother?